In today’s interconnected world, information gathering has become a vital step in cybersecurity and threat analysis. One of the most effective tools for Open Source Intelligence (OSINT) is The Harvester. This Python-based tool is widely used by security professionals to collect data from publicly available sources, helping organizations identify potential vulnerabilities and take proactive measures to protect their assets.
What Is "The Harvester"?
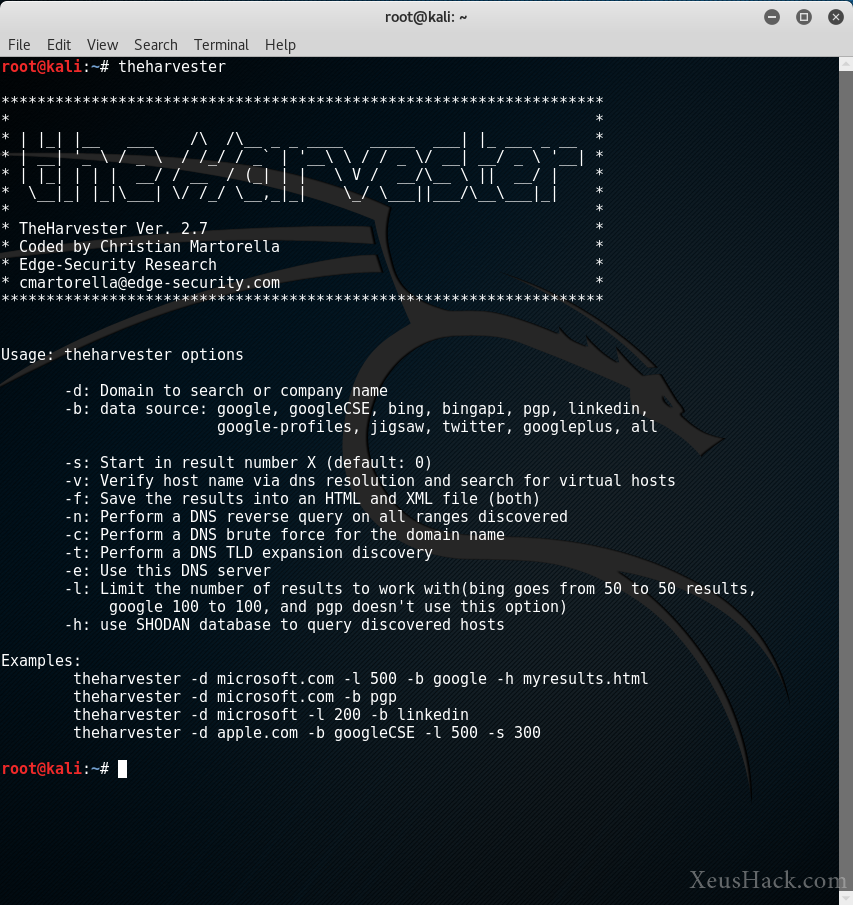
The Harvester is an open-source reconnaissance tool designed for gathering information about domains, emails, IP addresses, subdomains, and more. It works by leveraging publicly accessible data from search engines, social media platforms, and other online resources. This makes it invaluable for penetration testers, ethical hackers, and IT teams looking to bolster an organization's security.
Key Features
- Domain-Based Searches: The Harvester can extract valuable information about a specific domain, such as email addresses and associated IPs.
- Multiple Data Sources: It uses APIs and search engines like Google, Bing, Yahoo, and others to collect data. It also integrates with services like Shodan and PGP for advanced searches.
- Customizable Output: The tool can produce organized reports in various formats, making it easy to analyze the gathered information.
- User-Friendly Interface: Despite being a command-line tool, its syntax is straightforward, allowing even beginners to use it effectively.
Use Cases
- Cybersecurity Assessments: Security professionals use The Harvester during penetration testing to identify weaknesses in an organization’s public-facing infrastructure.
- Vulnerability Management: By identifying exposed emails or subdomains, IT teams can address potential entry points for cyberattacks.
- Competitor Analysis: Businesses can also use this tool to monitor the public information of competitors for market insights (always adhering to ethical practices).
How to Use
Using The Harvester is simple for those familiar with command-line interfaces. Here’s a quick overview:
- Install the Tool: Install via pip or clone it directly from its GitHub repository.
- Run a Basic Search: Execute a search by specifying a domain and a data source. For example:
theharvester -d example.com -b google
This will query Google for information related to "example.com".
- Analyze the Results: Review the output to understand what data is publicly accessible and take steps to mitigate any risks.
Advantages and Limitations
Advantages:
- Easy to use for gathering OSINT.
- Integrates with multiple data sources.
- Provides comprehensive information for free.
Limitations:
- Limited to the data available from public sources.
- Can trigger rate limits or CAPTCHAs on some services.
Conclusion
The Harvester is a must-have tool for anyone in cybersecurity or OSINT research. By collecting and analyzing publicly available data, it empowers organizations to understand their digital footprint and take steps to secure it. Whether you’re a seasoned security professional or a newcomer to OSINT, The Harvester is an excellent resource to add to your toolkit.
Note: Always ensure your use complies with ethical standards and legal regulations.
Tutorial The Harvester: https://www.hackerwebsecurity.com/the-harvester-raccoglitore/